The Search for the Dark Tower: Using OSINT to Hunt Down Magecart
10 April 2020
By Jacob Pimental
This will be a brief tutorial on using Open Source Intelligence (OSINT) to hunt down Magecart infections. I will go over some tools that could be used to pivot off of indicators and find new ones. I will also be giving a brief overview of my new tool, Gunslinger, and how it can be used to hunt for new infections.
OSINT
Open Source Intelligence (OSINT) consists of data that is publicly available on the internet. Normally this information is found from free sources, such as social media, public WHOIS entries, or free web scanners. In our case we will use public Domain information and HTTP Content to find more Magecart domains. The tools below are the ones I use to gather this intel.
RiskIQ PassiveTotal
RiskIQ’s PassiveTotal allows you to search for domains, IPs, ASNs, certs, etc. and will provide a ton of data on what you search for. You can also set up monitors on IOCs to see if infrastructure has changed (i.e. domain resolves to different IP). You can also use PassiveTotal to see other domains that an IP resolves to, which is useful for finding other malicious domains related to that campaign. The RiskIQ team have also published a few projects on there that are good jumping off points when starting your hunt.
URLScan
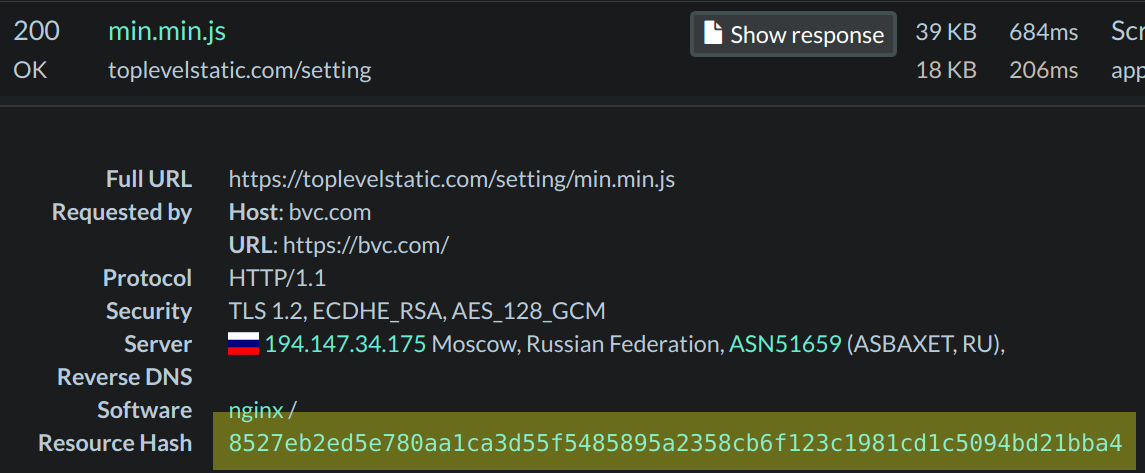
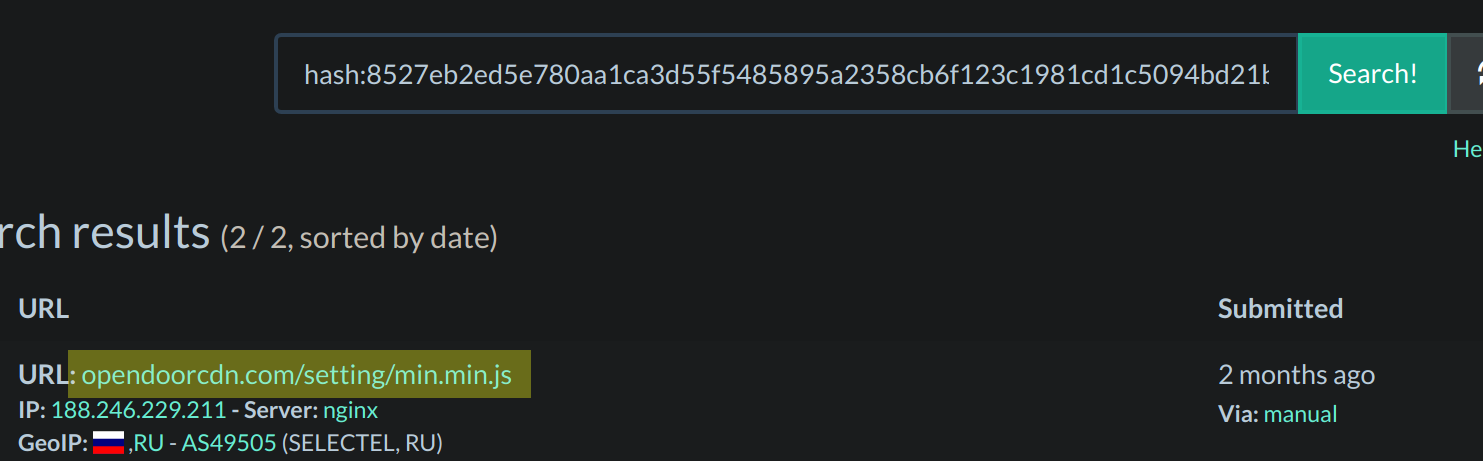
URLScan is my goto tool when looking into a possible Magecart campaign. It allows you to scan a site and see what network connections it makes. The feature that I use the most is its search capability. I can throw in a known Magecart domain and get back sites that link to it. I can also throw in a hash of a known malicious script and find other sites that are hosting it as well. This was the case with Magecart Group 12’s toplevelstatic domain from a previous article. It was hosting the same script as the Opendoorcdn, which was a good indicator that they belong to the same group.
Gunslinger
All of this was a manual process, and became very slow and tedious. I wanted to make a tool that would scrape recent URLScan submissions and report back any submitted sites that had Magecart on them. Thus Gunslinger was born. It uses URLScan’s search API to scan recent submissions for any Magecart infections. So far the tool has found several other Magecart domains, which I wrote about in my previous post.
Gunslinger runs on a set of user-defined “rules”. Instead of crafting my own language like yara, which was my original plan, I had it load python modules that the user created. This allows for more flexibility as the user can write a rule based on more than just the content of the script. Rules can be based on any data that URLScan passes back, such as URL, ASN number, geolocation, etc. An example rule is defined below
import re
def run(**kwargs):
reg1 = r'function ant_cockroach'
reg2 = r'cc_number'
reg3 = r'payment_checkout[0-9]'
script = kwargs.get('script', '')
ant_cockroach = len(re.findall(reg1, script)) > 0
cc_number = len(re.findall(reg2, script)) > 0
checkout = len(re.findall(reg3, script)) > 0
return ant_cockroach and cc_number and checkout
This was created based on the e4[.]ms magecart campaign. It looks to see if the script contains the function ant_cockroach, as well as for the term “cc_number” to show up in the script and “payment_checkout” followed by a number from 1 through 9. The module must contain the function run that uses kwargs to accept parameters. The parameters sent are script which contains the content of the scanned script, and response_data which is the URLScan API object related to the site (you can find more information about this on URLScan’s API Page). The use of user-defined rules allows Gunslinger to branch out from Magecart to hunting any JavaScript malware.
Currently Gunslinger sends reports to a Slack channel. It will send the original parent site that was scanned, as well as a list of the links that were seen and what rules they fired one. In the future I want to add other outputs, such as MISP and a generic HTTP POST request with the reported data. That way the user can intercept this and do with it whatever they want. Here is example output of a fake Flash Install script found on a Covid-19 map, caught by one of my rules:
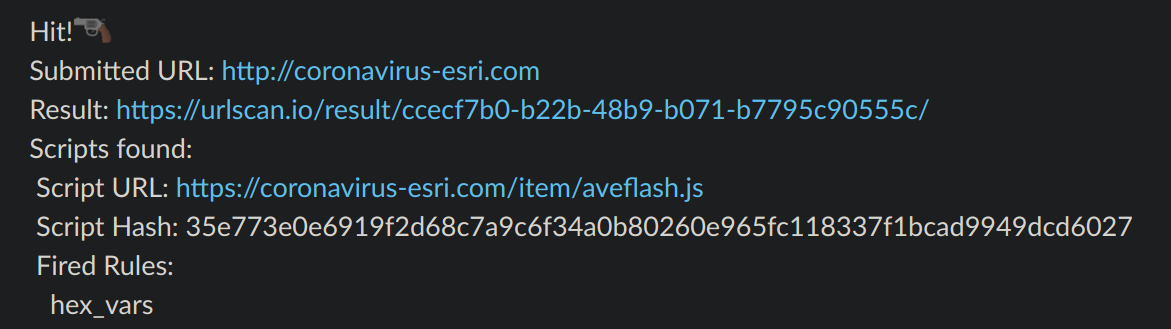
Conclusion
When used in conjunction, these tools work well in hunting down new magecart infections. I use Gunslinger to look for potential Magecart campaigns, URLScan to find all site that were hit by this campaign, and PassiveTotal to find other domains that might be related. I am sure there are many other ways to find new campaigns, I just wanted to share a few tools that have proven useful to me. If you like what you read I will also be speaking about this at SourceDefense’s MageCart webinar on April 30th. You can sign up for it here. If you have any questions feel free to reach out to me on my Twitter or LinkedIn.
Thanks for reading and happy reversing!