OpendoorCDN Skimmer Analysis Continued
03 February 2020
By Jacob Pimental
In my previous article I went over a joint analysis with Max Kersten about an Olympic ticket reseller website that was infected with a Magecart-like credit card skimmer. This article is a continuation of that, since we have more findings to share. This is also a joint analysis with Max Kersten, you can find his blog here. You can read the original post on this here.
Discovery
As mentioned in the original article, the malicious script that was found on the Olympic Ticket site reached out to the domain opendoorcdn[.]com. Max decided to look into this domain some more after our initial analysis was done. He found that the domain hosted the same skimmer as the one we initially found on the Ticket site at opendoorcdn[.]com/setting/min.min.js. Through more research it was discovered that several other sites were referencing this URL in their code, and thus were infected with the skimmer. You can see this on URLScan here.
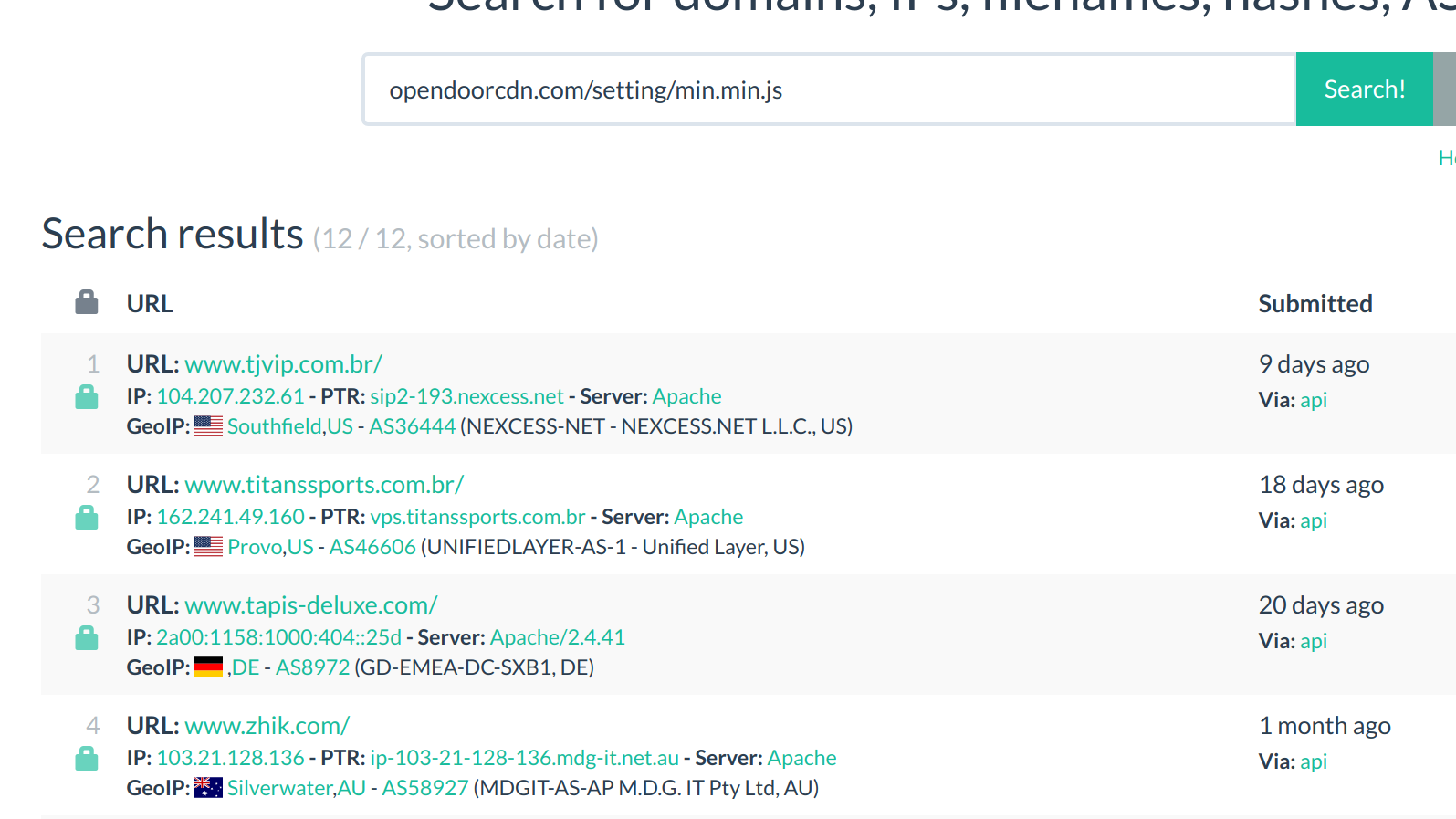
Some of these sites have been hosting the malicious script as early as October 12th, 2019. A few of these sites have already noticed the infection and removed any references to the script.
Here is a table showing which sites were infected, the earliest we saw that they were infected, and the last time the skimmer was seen on their site:
| Company | Site | First Observed | Last Observed |
|---|---|---|---|
| SupremeProduct | https://www.supremeproducts.co.uk/ | 12 Oct 2019 | 7 Nov 2019 |
| PartsPlaceInc | https://www.partsplaceinc.com/ | 13 Nov 2019 | unknown |
| Bahimi | https://bahimi.com/gbp | 19 Nov 2019 | 1 Feb 2020 |
| NaturalPigments | https://www.naturalpigments.eu/ | 1 Dec 2019 | Unknown |
| Zhik | https://www.zhik.com/ | 15 Dec 2019 | 21 Dec 2019 |
| Tapis-Deluxe | https://www.tapis-deluxe.com/ | 7 Jan 2020 | unknown |
| TitansSport | https://www.titanssports.com.br/ | 9 Jan 2020 | now |
| TJ VIP | https://www.tjvip.com.br/ | 18 Jan 2020 | 29 Jan 2020 |
| CDNN Sports | https://www.cdnnsports.com/ | 27 Nov 2019 | 12 Dec 2019 |
Differences in Tactics
I want to highlight the differences between this campaign and the one we saw on the Olympic Ticket website. The major difference is that the credit card skimmer script is NOT being hosted on the companies’ websites. Instead opendoorcdn[.]com is hosting the malicious code and is somehow being referenced by the victim sites. This follows more in line with how Magecart groups typically operate, meaning that this domain could be related to one of the groups.
Interesting Files
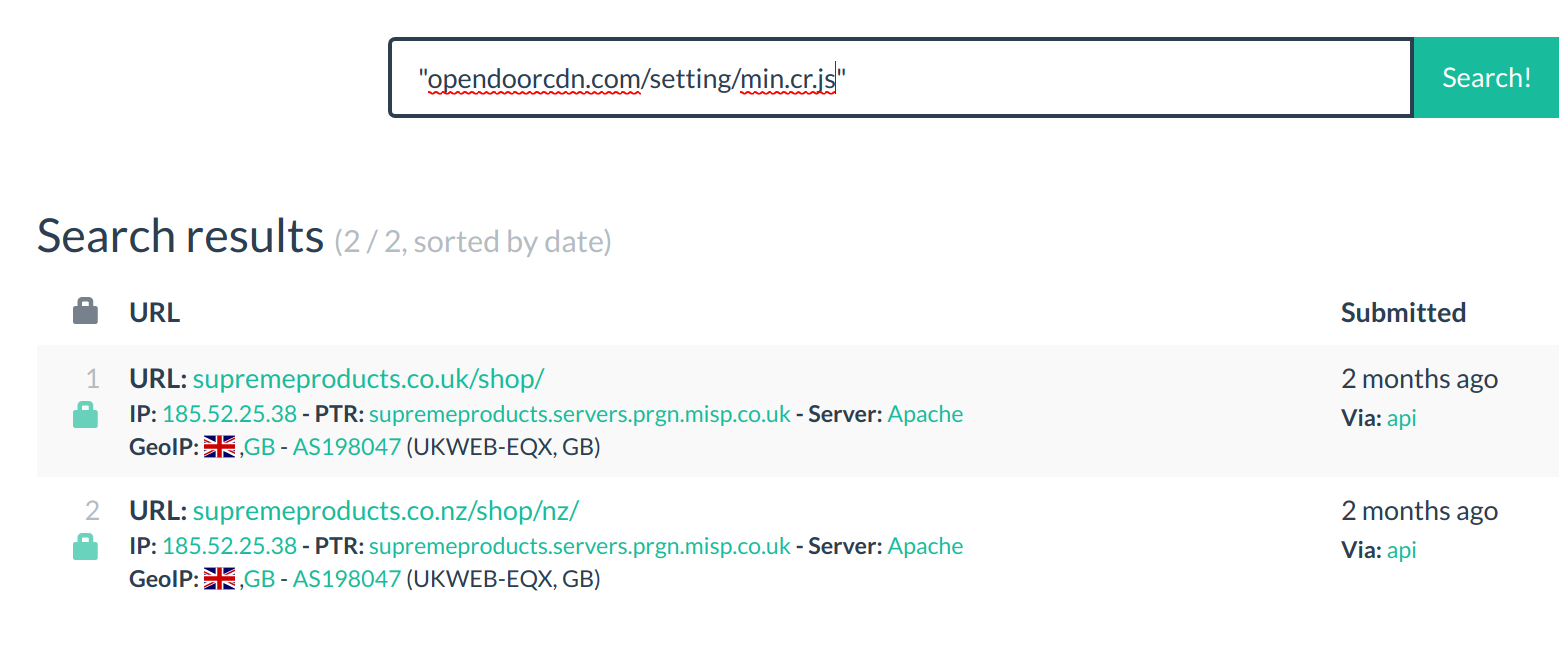
While analyzing the opendoorcdn website through URLScan, we stumbled upon a few other files of interest. The first being hosted at opendoorcdn[.]com/setting/min.cr.js. This appears to be another obfuscated skimmer, however when it is deobfuscated (thanks to Max for deobfuscating the code) it is the same as the original script we found. This version appears to have gone through the same obfuscation generator as the previous, except it has new variable names and a different hash. According to URLScan this file is only seen on the SupremeProducts site and not on the others. We are not sure the reason for this, whether it’s to evade AV detection or to fit in better with the site content.
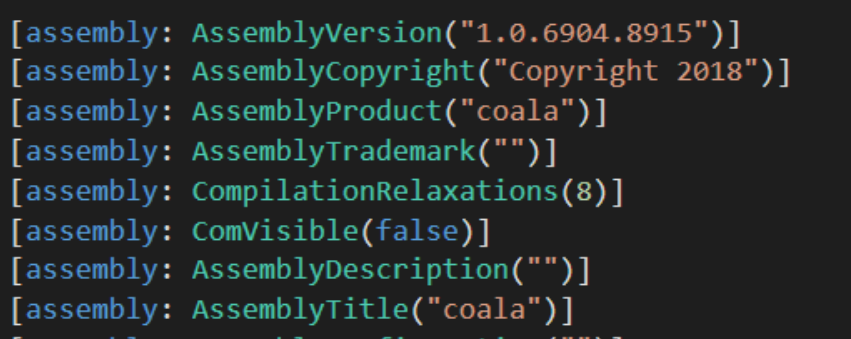
The second file we noticed was located at opendoorcdn[.]com/crfile/file.exe. This file is no longer being hosted on the website and returns a zero byte file when you try to download it. However, you can get the hash of the file that was hosted there 11 months ago via URLScan here. From there you can toss the hash into VirusTotal and grab the file from that. After a brief analysis it appears to be a packed .NET binary. If you run the binary and monitor the process in something like Process Hacker or Process Explorer you will see that it creates a new process called edge.exe. We can dump out this process using hasherezade’s pe-sieve with the command: pe-sieve /pid <pid>. If we throw the newly created dump into DnSpy we can see that it is a version of Coalabot.
Coalabot is like any other bot and will get commands from a C2 and run them. I thought this was very interesting for a magecart-like actor to also have hosted a malicious bot in the past. After monitoring the traffic from the bot in Wireshark I found these domains that the bot attempted to reach out to:
- goldchainsblue[.]com
- bookofbelgiumpoetry[.]com
- windows98fanclub[.]com
- windows2000fanclub[.]com
- makexpgreatagain[.]com
The only one that responded was makexpgreatagain[.]com, which was bought by a researcher to defend against this malware. It is not clear at this time whether these domains were also stood up by the same actor.
Disclosure
We decided it would be best to contact the websites that were infected with the skimmer and get them to remove them. Max sent the initial emails out on January 27th. As of right now we have not heard anything back from the companies and the ones that are hosting Magecart, still are. So far we have only seen TJ VIP, and Bahimi remove their references to the malicious domain on January 30th. That means as of the day this article was published, there are still two sites infected with the skimmer.
Domain Take Down
We also thought it would be best to take down the skimmer at the source. We looked into both where the server was hosted and where the actors registered the domain at. It appears that the server itself is hosted by Selectel, a Russian hosting provider. We felt that we would not have a very good chance of getting them to take down the server, so we looked into the domain.
We found the domain was registered to a Chinese company called Webnic, which has an abuse email that we were able to contact. Once contacted, telling them that one of their domains was hosting malicious content, they asked for a screenshot of what we saw. I responded to the email with a screenshot of the malicious skimmer code, along with linking our previous research into this campaign covered by BleepingComputer. After a few days of waiting they got back to me stating that the domain was taken down. This means that the references to opendoorcdn in the compromised websites are useless and the malicious actors won’t be able to inject their code into these sites.
Conclusion
Overall, this was an interesting look into the infrastructure this organization used to host their skimmer on more websites. It also shows that they have done more than just skimming, as they have hosted malicious executables on their site in the past. Also, be sure to talk to your bank about replacing your credit card if you have bought anything recently from any of the websites above, as your card may be compromised. I want to thank Max Kersten for helping me with this analysis and for discovering more sites that were infected. I would also like to thank Webnic for being very easy to work with and getting back to us in a timely fashion. As always, if you have questions or comments feel free to contact me on my Twitter or LinkedIn.
Thanks for reading and happy reversing!